
By: Montgomery Steen, Security Analyst, MAD Security | August 7, 2019
Overview:
Capital One has disclosed that a March 22-23 breach affected 100 million people in the US and a further 6 million in Canada. According to an indictment by the FBI, a software engineer in Seattle, hacked into an Amazon web server holding customer information for Capital One and obtained the personal data of over 100 million people, including Social Security numbers and bank account numbers. Included in the stolen data was tens of millions of credit card applications, 120,000 Social Security numbers and about 77,000 bank account numbers as well as one million Canadian social insurance numbers — the equivalent of Social Security numbers for Americans.
Method of Attack:
The perpetrator was able to gain access through a vulnerability in a web application firewall (WAF) that permitted privileged commands to reach and be executed by a service. This was then used to gain access to folders, or buckets, of data in Capital One’s storage space with AWS. AWS has stated that this was not an underlying issue with the AWS infrastructure, rather a misconfiguration of a WAF not specific to their cloud infrastructure. While we don’t have the exact details of the perpetrator’s exact methods, we are provided some generalized descriptions from the perpetrators Twitter posts:
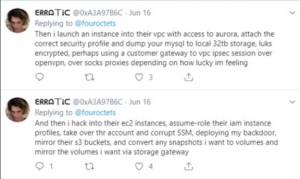
More clues were found in a Slack channel posting by the perpetrator, where a the following screenshot was posted.
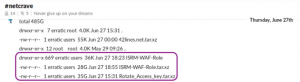
The names of the first two circled items coincide with information in the FBI indictment that indicate they could be the stolen material from Capital One. The first item is the name of a directory containing hundreds of items with the same name as the breached account, while the second is a compressed file of 28GB of data.
However, the name of the third item, “Rotate_Access_key.tar.xz” is a file of 35GB of compressed data and may also hold a potential clue to the hack. Access keys are required for Amazon IAM users in order to login to an AWS instance. AWS customers are advised to rotate these access keys on a regular basis. However, rotating keys, while not complicated, involves several distinct steps important for security. These include separate measures to ensure both that the previously used key is deleted and that the Secret Access Key required for key creation is recorded and stored securely. The Rotate_Access_key file in the data dump could suggest the keys were discovered prior to the breach and used to gain the required credentials. Alternatively, the file name could indicate the keys were discovered as part of the breach. It remains to be seen if more details are revealed as the case progresses through the courts. Either way, given the central role Access keys play in authentication in the AWS environment, the contents of “Rotate_Access_key.tar.xz” will undoubtedly be of interest to investigators in the case.
Recommendations:
The primary take away from the Capital One Data Breach is that enterprises need to ensure that firewalls and Web Application Firewalls are properly configured and maintained. Additionally, the following items should be considered:
- Harden systems before deployment using industry accepted best practices
- Regularly perform system audits to identify potential misconfigurations
- Ensure personally identifiable information (PII) data is protected with strong encryption
- On a regular basis engage third parties to do penetration testing to assist in identifying vulnerabilities and misconfigurations
- Limit the amount of access to the data to only those people and processes that require it
- Monitor for access to information systems to ensure only those permitted to access it are allowed,
- Employ a DLP solution to monitor for data leaving your environment
Sources:
https://www.cnbc.com/2019/07/30/paige-thompson-alleged-capital-one-hacker-stole-100-million-peoples-data.html
https://www.justice.gov/usao-wdwa/press-release/file/1188626/download
https://www.businessinsider.com/capital-one-bank-data-suspected-hacker-boasted-online-2019-7
https://www.capitalone.com/facts2019/

