
Managed Security Services
Increase Your
Security Posture while Controlling Costs
and Addressing Compliance Needs
Proactive, Cost-Effective Solution
As the cyber threat landscape becomes increasingly more sophisticated and our regulatory compliance requirements grow teeth, finding a way to protect network data, systems, and applications while ensuring compliance has become a top priority for most businesses. However, with depleting budgets and a shortage of expert security talent, this mission becomes difficult. MAD Security’s Managed Security Services provides a proactive and cost-effective solution for businesses to detect and respond to cybersecurity threats while ensuring compliance 24 hours a day, 365 days a year.
Managed Security Operations Center
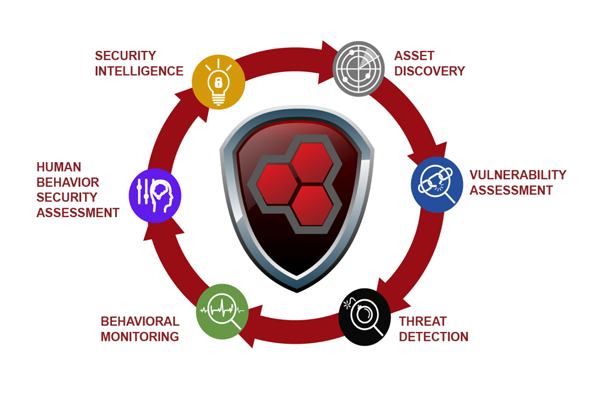
Asset Discovery
The first step to securing your environment is to obtain a thorough understanding of what is on your network. MAD Security discovers assets on your networks by using both passive discovery and active scanning techniques, in a non-intrusive manner.
- Passive Network
- Discovery
- Active Network Scanning
- Asset Inventory
- Host-based Software
- Inventory
Vulnerability Assessment
Finding and repairing vulnerabilities is a constant battle. MAD Security uses active network vulnerability scanning techniques to identify specific operating systems and services running on assets, as well as versions of software installed and their patches. This collected data is then compared to databases of known vulnerabilities, misconfigurations, known weaknesses, and compliance issues. In addition, continuous, passive vulnerability monitoring is layered on top of the active scanning, correlating the data gathered by asset discovery scans with known vulnerability information to provide context for security incident response and remediation.
- Continuous Vulnerability Monitoring
- Attack Vector/Avenue Identification
- Continuous Compliance Monitoring
Threat Detection
Over the years, hacking techniques have become more sophisticated and evolve daily, making detection and response difficult. Continuous monitoring is one of the most reliable methods for identification and tracking of attacks on your systems and data. Whether on the lookout for an unauthorized employee viewing confidential data or a malicious outsider trying to steal sensitive data, monitoring is indispensable for a strong security posture. Additionally, monitoring is a requirement for just about every major compliance framework and regulation, from PCI DSS to HIPAA and beyond.
- Network Intrusion Detection (NIDS)
- Host-based Intrusion Detection (HIDS)
- File Integrity Monitoring (FIM)
- 2,000+ Correlation Directives
- Hundreds of Threat Intel Data Feeds
Behavioral Monitoring
Preventative security measures are often unsuccessful with new polymorphic malware and zero-day exploits, making it even more important to be on the watch for intruders and nefarious activities. Behavioral monitoring for your network, systems, and users is essential for spotting these threats can be useful in investigating suspicious behavior and policy violations.
- Real-time Service & Infrastructure
- Monitoring
- Netflow Analysis
- Network Protocol Analysis & Packet Capture
- User Activity Monitoring
Human Security Behavior Assessment
Humans continue to be easy targets for attackers wishing to establish a foothold in your environment. The attackers are able to exploit these targets through clever phishing and spear-phishing tactics that prey on the trust and lack of vigilance present in most workforces. Having humans that understand information security and how to minimize security risk in daily operations greatly improves your organization’s ability to protect its sensitive information assets. We provide fully managed testing, analysis, and reporting on your organization’s human responses to simulated phishing attacks by combining phishing assessments with “teachable moments” to reinforce security awareness and learning, and ultimately your human behavior. Additionally, we integrate the results of these assessments into our monitoring platform to fine-tune and greatly improve our threat detection capabilities.
- Simulated Phishing Attacks
- Teachable moments reinforcing security awareness learning
- Results correlation with threat detection capabilities
Security Intelligence
Effective security intelligence provides the information necessary to detect threats and subsequently contain them. While it is impossible to eliminate 100% of the threats we face, reducing the time it takes to respond and contain them is certainly achievable. We focus on the processes and technologies used to detect compromises to coordinate the responses.
- Security Incident & Event Monitoring (SIEM)
- Log Management
- Security Event Correlation
- Incident Response
- Threat Intelligence
Threat Intelligence
VCM
Vulnerability Management Service
Our Vulnerability Management service performs continuous scanning within your environment to identify, detect, classify, and track vulnerabilities. This increases your security posture and enables the tracking and mitigation of risk, all while meeting the rigorous compliance requirements with ease.

User Awareness Training
MAD Security’s Managed User Awareness Training ensures your employees are meeting security awareness training requirements and are kept up to date on security threats. The effectiveness of this training is then verified through performing regular phishing assessments.
Phishing





