Risk and Compliance Service
Your Trusted Cybersecurity Partner
A Complete Portfolio of Compliance Solutions Tailored for Your Business.
Businesses turn to us for our ability to guide them in determining requirements, assessing cyber risk and compliance, and developing and deploying efficient cost-effective solutions. While most providers have a “check the box” mentality, our cyber risk and compliance experts take the time to understand, develop, and deliver solutions tailored for your business.
Delivering Exceptional Services to Our Valued Clients
Businesses are facing an ever changing and escalating risk landscape. For example: DoD Contractors have the DFARS regulation that started in 2017, and then needed to prepare for and gain understanding and insight into the CMMC certification, and now must adopt CMMC 2.0 to protect their contracts and maintain their ability to bid on future contracts.
It is imperative for executives and senior management to identify and understand the risks facing their business. Your business needs a team that can act as a trusted advisor and strategist to provide actionable roadmaps that not only improve your security posture and help mitigate risks, but also help develop and govern your Information Security program.
Cyber Risk and Compliance touches every part of a business. In doing so, it serves to provide a firm foundation for sound risk intelligence as well as a way forward to complying with new regulations and security controls.
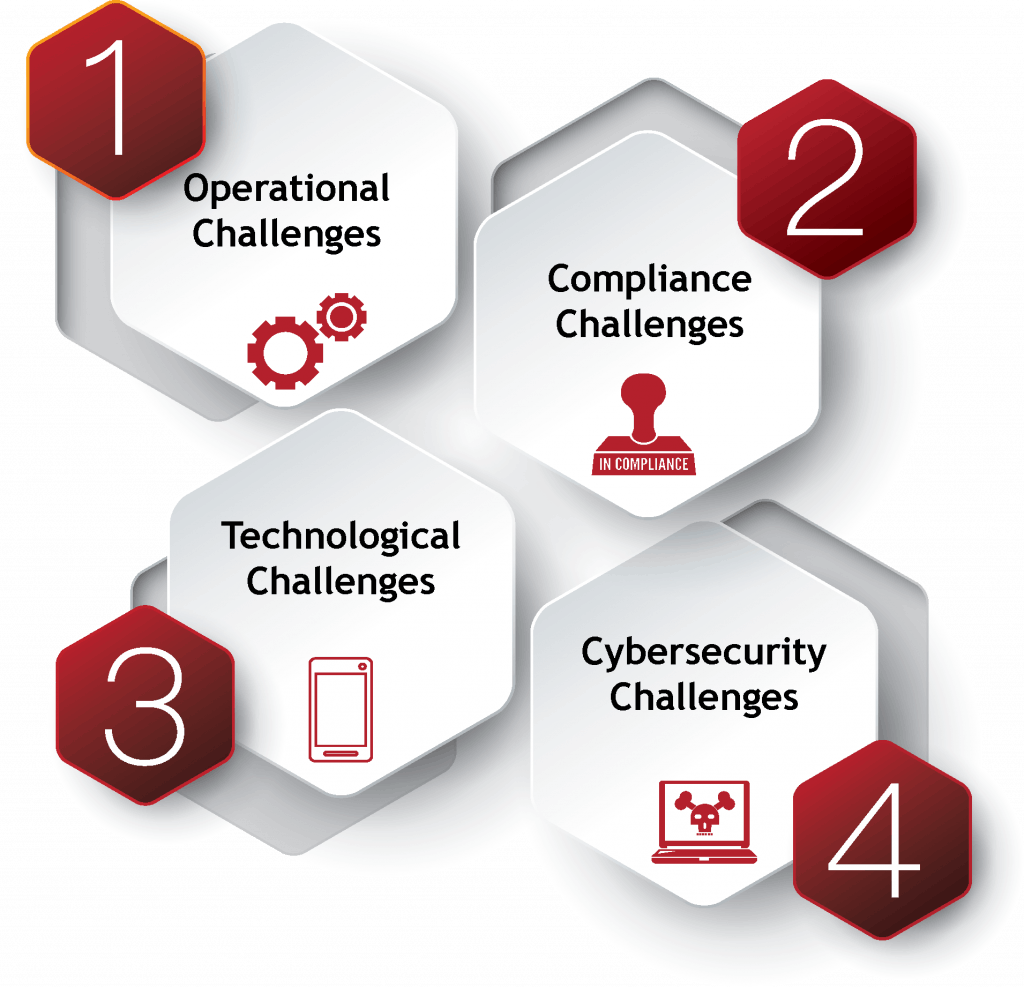
The Most Common Challenges We Help Businesses Solve
Compliance Challenges
- Ever-evolving regulations across multiple industries (e.g. Cybersecurity Maturity Model Certification (CMMC 2.0) for DoD Contractors)
- Political influences on regulation changes and priorities
- Penalties for lack of compliance and its effect on the organization’s reputation
Operational Challenges
- Assessing and understanding the current state of their security posture and building a roadmap for improvement
- Building a process for identifying, managing, and mitigating risks proactively
- Prioritizing changes based on risk and compliance requirements
- Quantifying return on compliance: How does this affect their bottom line?
- Transparency across the organization and managing functional silos
Technological Challenges
- Ensuring data privacy across devices, the organization’s network, and the cloud
- Ensuring all technologies are adhering to compliance requirements and risk management best practices
- Interconnectivity of Risk across the organization
Cybersecurity Challenges
- Highly disruptive ransomware
- Continued security breaches
- New Phishing techniques
- Compliance violations and regulatory actions