Risk and Compliance Service
Your Trusted Cybersecurity Partner
A Complete Portfolio of Compliance Solutions Tailored for Your Business.
Businesses turn to us for our ability to guide them in determining requirements, assessing cyber risk and compliance, and developing and deploying efficient cost-effective solutions. While most providers have a “check the box” mentality, our cyber risk and compliance experts take the time to understand, develop, and deliver solutions tailored for your business.
Top-Notch Complete Solutions
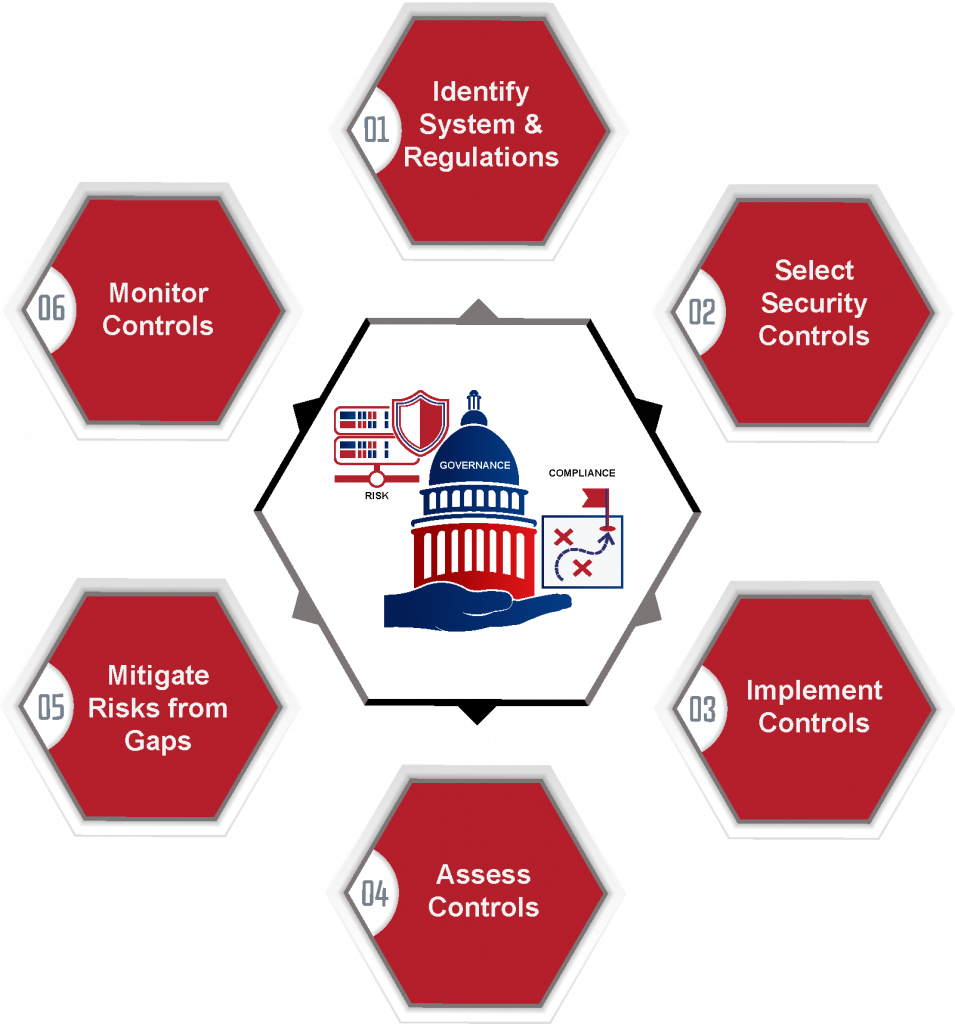
Today’s dynamic global business environments demand that you adapt quickly to changing regulations and to mitigate emerging risks. As business objectives are forced to become consistent with regulations, risk and compliance strategists should ensure that your security posture and strategy also align with regulations, governance models, and policies.
Our cyber risk and compliance solutions help to first understand risk tolerance and gaps, and then provide a plan of action to mitigate risks, achieve compliance, and maintain security posture through a Continuous Monitoring Strategy.
Tailored to your needs
Solutions that go beyond traditional compliance solutions helping to reduce risk, increase compliance, and address cybersecurity challenges unique to your business.
Gap Assessments
Risk Assessments
Identifies, evaluates, and estimates levels of risk to your organization and determines an acceptable level of risk.
Virtual Compliance Management
Continuously collaborates with you and your organization to ensure that your cybersecurity program is being maintained within compliance regulations and that security controls are monitored continuously. Ongoing reviews and assessments will help to ensure that controls that are not fully implemented are on track for mitigation, as well as ensuring that implemented controls are maintained and reviewed.
Risk
Creates a standard designed to assist with managing the confidentiality, integrity, and availability of data and critical infrastructure.
C-Suite Consulting & Virtual-CISO Consulting
Allows organizations to leverage top-tier security experts with CISO-level experience for security strategy sessions and guidance.
Business Continuity & Disaster Recovery
Ensures that cybersecurity concerns are incorporated into your Business Continuity and Disaster Recovery planning to minimize costs, protect data, and streamline a timely and effective response to any kind of attack.
Policy Development & Review
Creates a policy development workflow and review process formulated around what governs an organization to ensure regulatory compliance.
Information Security Governance Framework Design
Creates a framework that ensures information security strategies are aligned with and support business objectives, are compliant with applicable laws and regulations, and that integrate with an organization’s governance at the highest levels.