
For many businesses, compliance is becoming a way of life. As cyber-attacks and data breaches are revealed and reported on a regular basis, new compliance requirements will continue to be implemented. A couple of recent examples are the NIST 800-171 (Defense Federal Acquisition Regulation Supplement or DFARS) requirements for Controlled Unclassified Information (CUI) and GDPR regulations for protecting personal data of EU citizens. In this post, we’ll focus on NIST 800-171, what we can expect from it this year, and how to maintain compliance throughout 2018 and beyond.
NIST 800-171 and its Implications for 2018
Since the December 31st deadline has come and gone, many defense contractors and subcontractors may be curious as to how it will affect them. If a defense contractor currently has an existing defense contract that includes the DFARS clause, then they must already be on the road to compliance with their System Security Plan (SSP) and Plan of Actions and Milestones (POA&M) in place. Also, if a contractor plans to bid on a similar contract in the future, they must also have begun this process.
However, just creating a POA&M and an SSP is not a “set it and forget it” thing. A contractor must show continual improvement. This is where a Continuous Monitoring Strategy (CMS) comes into play. A contractor should be working to close the gaps identified in their initial Gap Assessment by completing tasks and fulfilling obligations on schedule within the POA&M, updating their SSP, as well as continuing to monitor their environment.
DFARS consists of 14 families of controls totaling 110 controls, which can be found in the NIST Special Publication 800-171 here for reference.
Staying Compliant with AlienVault’s USM Managed by an MSSP
As you drill into the control families it may become obvious that many of the controls can either be supported by, if not fully covered by, an established MSSP delivering services using AlienVault technology. Take for example Access Control – this control family covers best practices relating to controlling access within the environment. This includes limiting access to systems and data to authorized users, ensuring elevated privileges are not misused, and ensuring cryptographic mechanisms are used to protect confidentiality. It also includes ensuring that all sessions and connections are authorized and monitored. All of these controls can be effectively monitored using AlienVault technology and fully controlled leveraging the services of an MSSP.
An added benefit to using AlienVault technology, is its reporting features. If you’ve ever been through any type of compliance audit you know very well that it isn’t only being compliant that is a pain point, it’s providing the evidence that you are. An MSSP simplifies this for you by leveraging AlienVault to map associated events to each control family, allowing you to easily provide your auditor with strong supporting evidence of your compliance.
This type of support makes ensuring and proving compliance a much less onerous task.
How an MSSP Can Fill Compliance Gaps
When it comes to compliance, technology is not a panacea, as there are always processes and procedures required. This is why partnering with an MSSP can be beneficial, as technology in the hands of a skilled and trained professional can not only enable your compliance, but likely make boost your security posture by operationalizing compliance requirements.
An example of this can be found in the Awareness and Training control family within DFARS. This control family covers best practices for ensuring that employees areproperly trained and aware of security threats. To be fully compliant with this control family you must demonstrate that employees are aware of security best practices, are applying security awareness to their daily jobs, and know the proper processes and procedures to take in case of a potential compromise or security incident.
Why is this so important? Well as you likely already know, humans continue to be easy targets for attackers wishing to establish a foothold in your environment. In many cases these attackers do so using clever phishing and spear phishing tactics that prey on the trust and lack of vigilance across your workforce. Having employees educated on information security and how to minimize security risk in their everyday activities greatly improves your organization’s ability to protect its sensitive information assets.
With this importance in mind, how could an MSSP using technology help to ensure our personnel are trained adequately to recognize security risks and know to follow the proper reporting procedures? A properly implemented phishing engagement testing users on both fronts is one of the simplest methods.
Based on our experience, one of the most effective and simple scenarios is sending a spoofed LinkedIn request. Targeted users receive an email that appears to be a connection request from LinkedIn; like the following, but customized to look like any user depending on the pretext of the scenario.
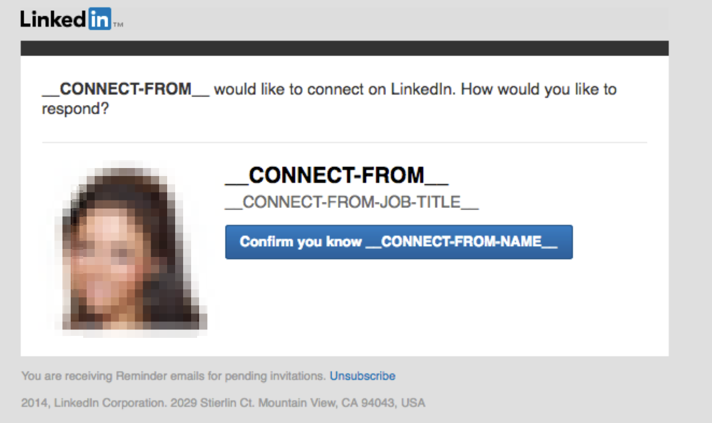
Once the user attempts to confirm the request they will be taken to a fake login website for LinkedIn.

This website will likely be a lookalike domain, such as “linkedin-accounts.com”. Each individual act performed by the user including opening and reading the email, visiting the fake website, and submitting their information will be logged and tracked. Alternatively, a user can be redirected to a training page for immediate security awareness training, or if requested, to the real LinkedIn login page to avoid suspicions and lower the likelihood of the user informing other co-workers of the training being conducted.
It is likely obvious now how a capable MSSP can fill in the gaps where technology itself may come up short. By collecting, analyzing, and reporting on the statistics of where your users are susceptible to these types of attacks and at what stages of the attacks they were diligent in reporting issues to you, an MSSP can help shape and scope your security awareness control family controls – and at the same time increase your security posture.
It doesn’t need to stop here though, as compliance, training and information alone doesn’t always make things operational. A mature and very capable MSSP using AlienVault technology will take this one step further by ingesting the information to make it actionable. By using the statistics gathered, defined as the vulnerabilities identified in the humans within your environment, and combining this data with the risk scoring and alarming capabilities within AlienVault technology, an MSSP can raise their situational awareness to not only track system assets and vulnerabilities, but human assets as well.
You can also find this blog published on our partner’s website here.

